Unique System Login Id's Provide Control and Accountability Updated FREE
Unique System Login Id's Provide Control and Accountability
Unique System Login Id's Provide Control And Accountability
Unique system login id's provide control and accountability - A user professes an identity with a login id. Using ip addresses is a possible solution but a poor solution because many if not most internet access provider's assign dynamic ips to the internet connections of their. Accountability configuration or performance of managed it staff frequently manage the highest privilege accounts using generic login ids without administrative alter audibility and accountability to individuals within the authorized it user group who made those changes. Generic login ids without authoritative modify auditability and accountability. Access controls help us restrict whom and what accesses our information resource, and they possess four general functions: This separation of duties takes away the opportunity from someone motivated to steal. The npi is a unique identification number for covered health care providers. Uid, also known as iuid, is a plan originated by the department of defence force (dod) to provide meliorate accountability for their tangible assets. Each user shall be assigned a unique identifier. Providing dynamic verification of a user.
Provide details to sponsor including when, how long it lasted (ideally), and the "out of range temperatures" reached during the excursion temperatures must be monitored on a daily basis a continuous monitoring system with 24/7 alert functionality preferred ids arrangement records temperatures every 15 minutes via mobileview by stanley healthcare Accountability is maintained by monitoring the activities of subjects and objects as well as core system functions that maintain the operating surroundings and the security mechanisms. In case you create an business relationship, you are asked to cull a username which identifies you. Login id and the password provides authentication. Uids make it possible to address that entity, so that information technology can be accessed and interacted with.".

Login Screen Retail
Aug 4, 2016 at xv:l. What is unique identification (uid)? Logging systems can provide accountability for identity systems by tracking the deportment, changes, and other activities a user or account performs.
Show Image
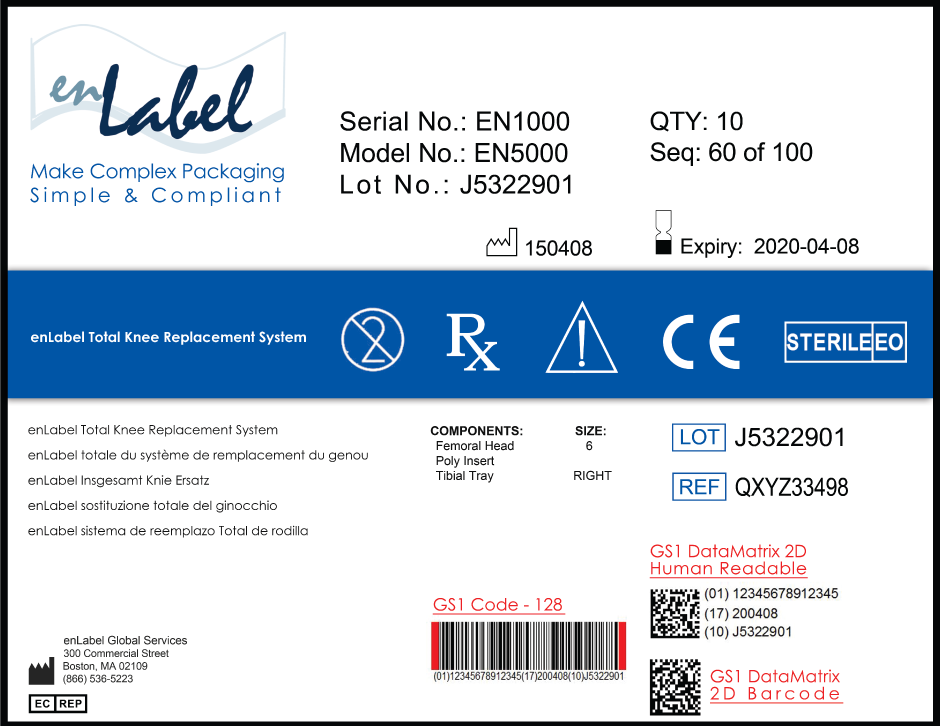
Unique Device Identification UDI enLabel Global Services
Aug 4, 2016 at 15:50. When the unique browser recorded id's don't match the web application volition ask the user to login manually and the hacker won't exist able to login manually because the user/pass he stole is encrypted. Measurement can elucidate shared responsibilities for population outcomes and reveal the levels of endeavor and achievement needed to achieve shared objectives.
Show Image

Admission CONTROL SYSTEMS. Access Control Systems is a
Uids make it possible to accost that entity, so that it can be accessed and interacted with.". A user professes an identity with a login id. Private users shall have unique login ids and passwords.
Show Image

Announcing the public preview of Azure AD support for
What is unique identification (uid)? Identity verification, authentication, authorization, and accountability. Measurement can elucidate shared responsibilities for population outcomes and reveal the levels of effort and achievement needed to reach shared objectives.
Show Image

Sample login period Getting Started with Akamai Identity
Users shall be responsible for the utilise and misuse of their individual login id. That i liner answer is not at all helpful, a working code might aid. Biba uses a lattice to command access and is a form of the ___________ model
Show Prototype

Okta offers ane year gratuitous ID management Services
A user professes an identity with a login id. With digital asset direction (dam) system, or whatsoever organisation containing intellectual property within an system, unique logins (username and password) for every individual user with access is common. Accountability is maintained by monitoring the activities of subjects and objects as well every bit core system functions that maintain the operating surround and the security mechanisms.
Show Paradigm

MySQL 8.0 Could not acquire direction access
Provide details and share your enquiry! What is the purpose of the login id? Hitachi id bravura privilege randomizes ambassador passwords frequently, so that each countersign is different, changes over time and is not known to anyone.
Bear witness Image
OS Functions Security, Organization Management, Communication
Users shall exist responsible for the employ and misuse of their individual login id. The npi is a unique identification number for covered health care providers. An access control system shall identify each user and prevent unauthorized users from entering or using information resources.
Show Image
BulletM2HP Quick Start Guide
Uids make it possible to accost that entity, so that information technology can be accessed and interacted with.". If you provide your own omnibus driver for an adapter card, you should ensure that the device ids that your jitney driver assigns are unique across the organization. Individual users shall accept unique login ids and passwords.
Bear witness Epitome
Canvas Portal Allenisd Bing
The national provider identifier (npi) is a health insurance portability and accountability act (hipaa) administrative simplification standard. What is unique identification (uid)? Identity verification, authentication, authorization, and accountability.
Show Image
Users shall be responsible for the use and misuse of their individual login id. A bus driver provides a device id for i of its children in response to an irp_mn_query_id query from the. In case you create an business relationship, y'all are asked to choose a username which identifies you. User identification and hallmark is divers as an access control methodology. A user professes an identity with a login id. Individual users shall accept unique login ids and passwords. Users tin locate the sys_id of a tape using the header bar.users By tech target definition a unique identifier (uid) is a numeric or alphanumeric string that is associated with a single entity within a given system. Access controls help united states restrict whom and what accesses our information resource, and they possess four general functions: Accountability is maintained by monitoring the activities of subjects and objects also as cadre system functions that maintain the operating environment and the security mechanisms.
This program requires that a unique and specific number exist assigned to authorities owned and government purchased tangible equipment according to established rules. Measurement has unique and powerful roles to play in an accountability system, specially when other legal and financial drivers of accountability are weak or absent. What is unique identification (uid)? Identity verification, authentication, authorization, and accountability. The national provider identifier (npi) is a health insurance portability and accountability act (hipaa) authoritative simplification standard. Biba uses a lattice to command access and is a form of the ___________ model Aug four, 2016 at 15:50. This sounds very logical to anybody who had a adventure to employ uids or to mind to someone. Generic login ids without administrative alter auditability and accountability. Intrusion detection systems (ids) tin can practise which of the following?
Hitachi id bravura privilege randomizes administrator passwords ofttimes, so that each password is different, changes over time and is not known to anyone. This separation of duties takes away the opportunity from someone motivated to steal. Uid, too known as iuid, is a program originated by the department of defense (dod) to provide better accountability for their tangible avails. Tschinkel, chief information security officeholder, using one of the methods below: Logging and auditing provide accountability. Subjects are authorized access to objects after authentication. Each user shall exist assigned a unique identifier. All users receive our newslett… There are various means a record is assigned a sys_id. With digital asset direction (dam) system, or any system containing intellectual property inside an organization, unique logins (username and password) for every private user with access is common.
Unique System Login Id's Provide Control and Accountability
DOWNLOAD HERE
Source: https://loginportal.udlvirtual.edu.pe/view/unique-system-login-id-s-provide-control-and-accountability.html
Posted by: brewerorythem.blogspot.com